I recently heard in one of my tech groups on the Matrix network about a new app suddenly appearing on many Android devices: Android System SafetyCore. ?
At first, there was a lot of confusion – some suspected malware, others thought it was a buggy update. But it quickly became clear: this isn’t some shady download, but rather an official Google system app silently installed on devices without any visible announcement.
And that’s where the problem begins: when a company like Google rolls out background features that deeply integrate into the system, the question inevitably arises – is this really about safety, or also about control?
What does the app actually do?
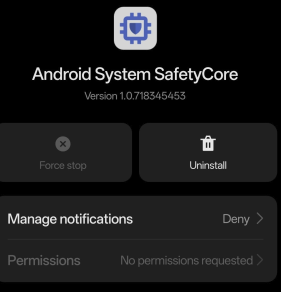
SafetyCore is an invisible system service, embedded deeply within Android. It acts as infrastructure for on-device machine learning. According to Google, the app is initially being used in Google Messages – where it automatically detects images that may contain sensitive content such as nudity.
Here’s how it works:
- If you receive an image with possible “sensitive content,” it’s first blurred.
- A warning ? appears with information and support resources.
- You then decide whether to view the image or block it.
- The same applies when sending images – if nudity is detected, you’ll be warned before sending.
Google stresses that this analysis happens only on your device (on-device), and images are not uploaded to servers. Technically, SafetyCore provides the recognition modules that apps like Messages can call upon.
Planned future functions include:
- Detecting dangerous links in chats
- Blocking messages from unknown international senders
- Classifying content as spam, fraud, or malware
Why I find this problematic ⚠️
- Installed without consent
SafetyCore was rolled out automatically, with no prior request or notification. - Lack of transparency
Google only mentioned the app in a blog post. Most users discovered it when digging through their system app list. - Potential for abuse
Even if Google currently claims no data is sent to servers, the technical groundwork is there. This could change in the future. - Undermining end-to-end encryption
In theory, apps like SafetyCore can weaken the concept of end-to-end encryption. Why? Because content is scanned before it is encrypted and sent. The encryption remains intact, but if messages or images are analyzed on the device prior to encryption, the real protective value is compromised. - Erosion of personal freedom
My phone belongs to me. I shouldn’t be forced to accept hidden apps that inspect my content – even if they are supposedly “for my protection.” - Privacy law concerns
Under European GDPR rules, installing apps that process sensitive data without clear consent is questionable at best.
What the community says
The reactions are divided:
- Some see SafetyCore as a useful tool to fight scams and unwanted content.
- Others compare it to spyware, since it installs silently and integrates deep into the system.
- Most interestingly, GrapheneOS – an alternative Android system for Google Pixel devices focused on security and privacy (see this blog post) – does not install SafetyCore at all. Its developers emphasize that SafetyCore is designed for classification tasks (spam, malware, phishing) but not for reporting illegal content. They stress that making such a distinction is crucial to protect privacy and prevent false positives.
What you can do ?️
- Locate the app: Settings → Apps → Show all apps → Three-dot menu → Show system apps → search “SafetyCore”
- Disable it: In many cases, you can at least disable the app or remove updates.
- Stay alert: SafetyCore can reappear with future updates.
Conclusion ✍️
I believe security is important – but not at the cost of freedom and privacy.
SafetyCore might be well-intentioned, but its silent rollout breeds mistrust.
While systems like GrapheneOS deliberately avoid hidden installations and give users full control, Google silently installs an app that inspects your content – no matter how “local” the analysis may be.
Even more worrying is the fact that such a system can effectively weaken end-to-end encryption: if content is analyzed before encryption, the core principle of secure private communication is undermined.
Your smartphone should remain your space of self-determination – not a black box where hidden functions run without your knowledge or consent.